Wanna rule the world?
Simply join these boards ...
Or, if you find it inconvenient
to free up a spare $100 billion
to join one those boards, here's another way for you to influence the governance of
the world's information infrastructure ...
to join one those boards, here's another way for you to influence the governance of
the world's information infrastructure ...
Osmio is here to put individual human beings like you and me in
control of the world's information infrastructure.
control of the world's information infrastructure.
We invite YOU to participate in the governance of Osmio.
But first, watch these videos to learn what Osmio is all about.
For starters, Osmio is a
PKI Certification Authority
Let's take a look at what that means ...
Here's the amazing PKI construction
material that the solution is made of:
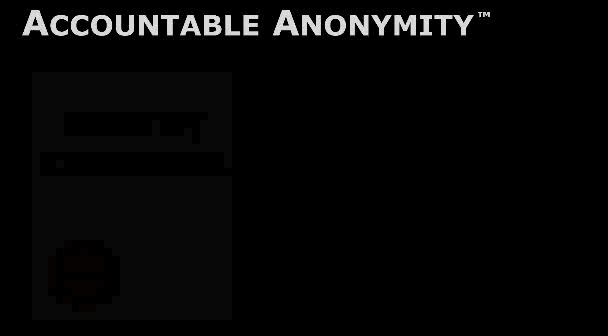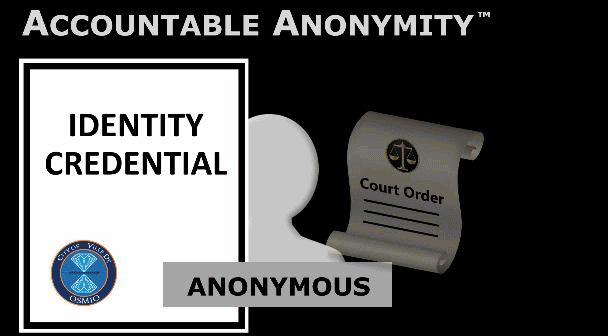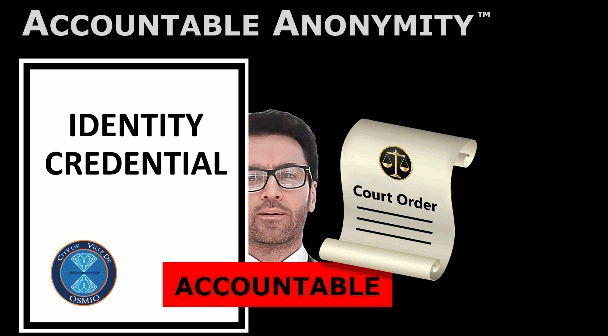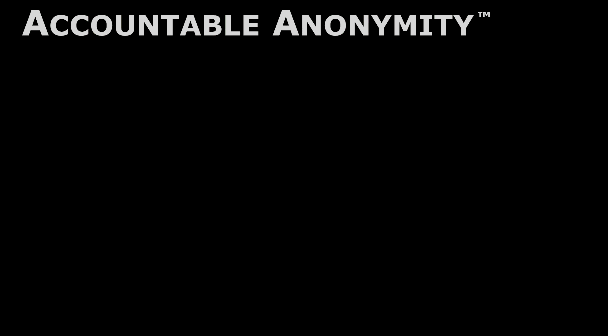
Something different:A non-commercial, non-political,
citizen-owned certification authority.
PKIDR™ workswhere
SECURITY TECHNOLOGY has failed us.
We're building a PKIDR™-based Information infrastructure
that supports real SECURITY, real PRIVACY, and real ACCOUNTABILITY.

© 2011-
The City of Osmio





